A detailed explanation of how attackers use Man-in-the-Middle (MitM) to hack WordPress websites and login credentials. This article is for educational purposes only.
Like any other web application with a login form, WordPress submits your username and password in an HTTP request when logging in. By default, HTTP is not an encrypted protocol. That means that unless your WordPress website is using HTTPS, the communication between you and the web server is susceptible to eavesdropping.
Hackers with malicious intent can easily intercept and modify your WordPress website’s cleartext (un-encrypted) HTTP traffic. Naturally, one of the most interesting pieces of information for an attacker would be your WordPress administrator credentials.
The software used to conduct Man-in-the-Middle (MitM) attacks is freely and widely available. This article will cover some real-world examples of how MitM can be used to take control of your WordPress website. Then it recommends how best to defend against them.
What is a Man-in-the-Middle (MitM) attack?
A Man-in-the-Middle (MitM) attack is a general term for attacks where a hacker positions themselves as an intermediary in-between a sender and a receiver. For example, between your browser and the website you are visiting. This allows the attacker to eavesdrop, and in many cases, also modify the content as it is sent and received between the two parties. In most cases, if they capture the credentials they can log in and hack your WordPress website.

How does an attacker get in the middle?
Man-in-the-Middle (MitM) attacks typically (not always) involve an attacker being on the same Local Area Network (LAN) as you. One of the most common MitM attacks involves ARP spoofing. The nitty-gritty details of ARP spoofing are beyond the scope of this article. However, the result of a successful ARP spoofing attack would result in your network switch or router being tricked into thinking that the attacker’s machine is your machine and vice-versa.
The result of this is that instead of each party sending data to each other directly, they first send it to the attacker. To make things seem normal, the attacker forwards the traffic to the rightful destination. However, this gives the attacker the ability to inspect and even modify the contents of the transmission.
Hacking WordPress websites – stealing passwords & login credentials
In order to understand how WordPress credentials would be stolen, let’s first look at an HTTP request containing submitted credentials using the browser’s in-built developer tools.
Note that this is not a Man-in-the-Middle (MitM) attack, but this helps illustrate what to look for later.
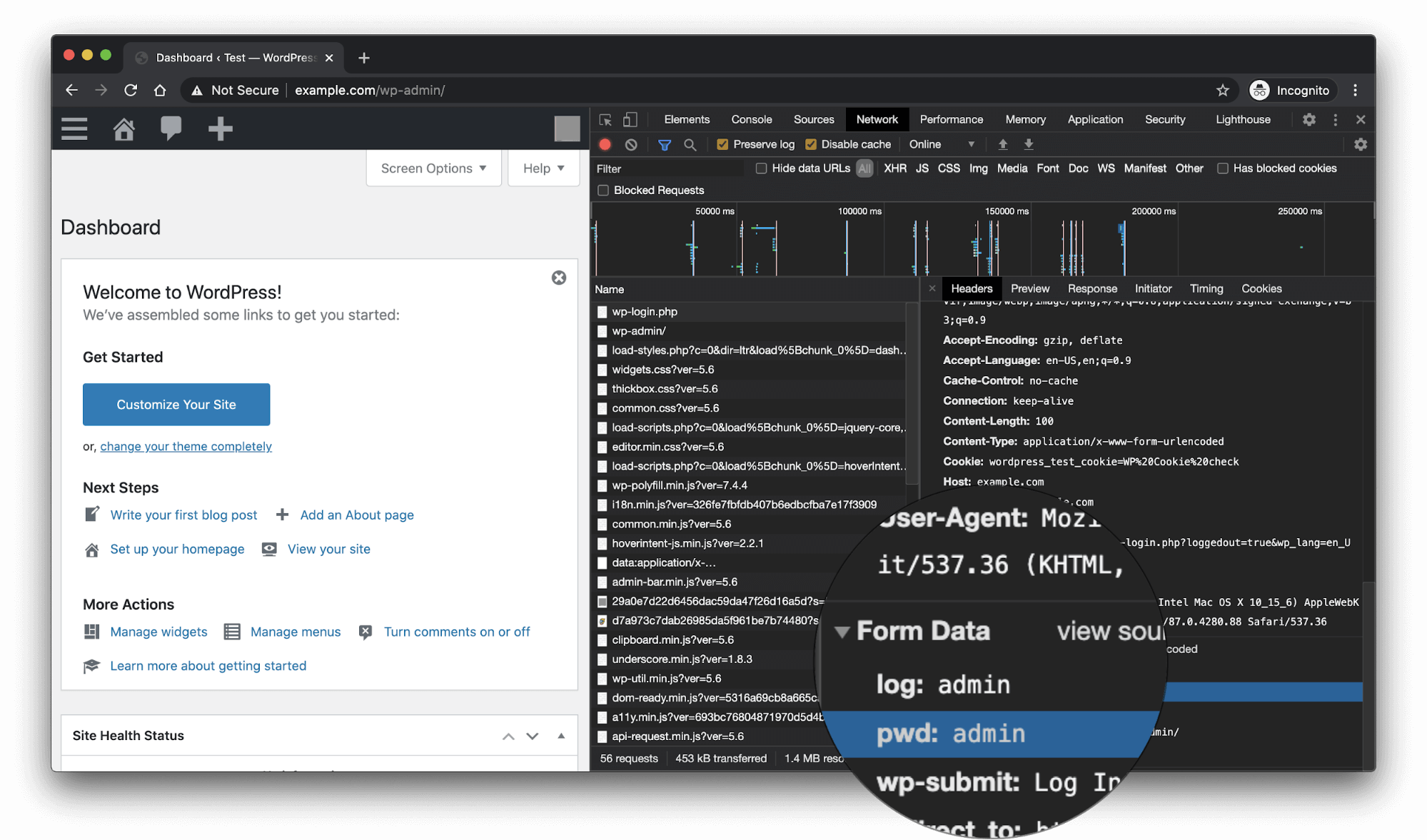
Now let’s take a look at what an attacker would see when inspecting unencrypted HTTP traffic. In this example we are using Wireshare, is a free and popular network analysis tool.

Stealing authentication cookies
In addition to stealing WordPress passwords / credentials, an attacker can also simply steal your authentication cookie to impersonate you.
How do cookies relate to authentication?
HTTP is a stateless protocol. In HTTP the server does not attach any special meaning to requests arriving over the same TCP socket. This means that unless you want to type in your password every time you request a page, the browser needs to store a temporary token. This token is known as a session token. The browser sends this token automatically with each and every request. Luckily, browsers have a built-in mechanism for this — cookies. That’s why deleting your browser cookies will get you logged out of all websites.
What this implies is that an attacker doesn’t even need your password to impersonate you. The only thing they need is to get a hold of your session token.

Once again, the same information is accessible to an attacker within Wireshark.

Using a free browser extension such as Cookie-Editor, an attacker can easily use the value of the stolen cookie in their browser and start browsing the WordPress admin as you.
Protecting yourself / your WordPress website from MitM attacks
Man-in-the-Middle attacks such as the one demonstrated in this article are very low-effort for an attacker to pull off. Especially in public or poorly secured networks such as a public WiFi. Luckily, protecting yourself from these hacking attacks is very straight-forward — make sure to enable and enforce HTTPS on your WordPress website.
HTTPS encrypts the traffic between your browser and the server. If an attacker had to attempt to read the contents of HTTPS traffic, all they’ll see is a lot of meaningless, garbled encrypted text.

Additional WordPress security hardening precautions
While you should unquestionably enable HTTPS on your website as your first priority to thwart Man-in-the-Middle (MitM) attacks, the following are good best practices when it comes to WordPress security and hardening.
- Add two-factor authentication (2FA) to boost the security of your WordPress website authentication mechanism
- Enforce strong WordPress passwords to make password guessing attacks significantly harder
- Limit failed login attempts on WordPress to thwart attacks such as DDoS and password guessing attacks
- Keep a WordPress activity log to monitor for unauthorized access to the WordPress admin
- Install a WordPress File Integrity Monitor to detect malicious file changes to your WordPress installation
- Set up a WordPress firewall and security solution to thwart common web application attacks.



