Every year, hundreds of thousands of WordPress blogs and websites are hacked. This leads to the question, how do I know if my WordPress site is hacked?
How do I tell if my WordPress site is hacked?
Sometimes it is very easy to tell, especially if a website is defaced. But most of the time, malicious hackers do a very good job at hiding their activity. In many cases, it takes weeks for businesses to realize their website is hacked. Sometimes it takes months or years!
Follow these tips to check if your website is hacked or if you suspect it is hacked. The sooner you identify a hack attack, the easier it is to recover it and the less damage is done.
Keep an audit trail to monitor users & under the hood activity on WordPress
A good indicator of a hacked WordPress website is unusual user activity, such as creation of new users, existing users’ password changes, user role changes, unapproved new content and modification of existing content. It is impossible to track such under the hood WordPress activity, especially on a multi-user blog unless you use a WordPress activity log plugin. A plugin such as WP Activity Log is very easy to use – just install it, and it automatically keeps track of all the changes that happen on your WordPress website.
Run frequent malware scans
There are a number of online services that provide malware scans, some of which can scan a few pages for free.
For example you can try the free Sucuri SiteCheck. This free scanner scans your website for a number of known WordPress security threats such as malware infections, spam, irregular redirects and several other issues typically found on hacked websites. In most cases, the free Sucuri SiteCheck will do the job, even though they only scan a limited number of pages.
Monitor WordPress files for changes
Malicious hackers inject malware on a WordPress website, or embed a backdoor by modifying the source code of the web application (WordPress). So another great way to identify malicious hack attacks is to scan your WordPress for file changes. The process of scanning your website for new, deleted or modified files is called file integrity monitoring (and scanning).
When you scan your site for file changes look for new files in the web root, modified index.php and functions.php files, new redirect rules or changes in the .htaccess files to infected domains and similar. If you can, search your entire file structure for strings such as “base64” to check for encoded code.
Monitor website traffic
The traffic of your website is another good indicator of a successful hack attack. Keep an eye out for unusual activity in website traffic, such as sharp increases or decreases. For example, if an old blog post or page that never ranked well suddenly becomes very popular for no apparent reason, it might be infected. If your WordPress site caters for the European market, and suddenly there is a burst of traffic from non-European countries, that as well can be an indication that something is wrong with your website.
You can watch closely your WordPress site traffic and ranking activity by using tools such as Google Analytics and Google Search Console.
Notifications in Google Search Console and web browsers
There are several benefits to adding your website to the Google Search Console. One of them is it monitors your website for malware and other types of infections. The Google Search Console alerts you via email if it identifies a malware infection on the website. Google also displays the below warning sign to visitors who are trying to visit your website.
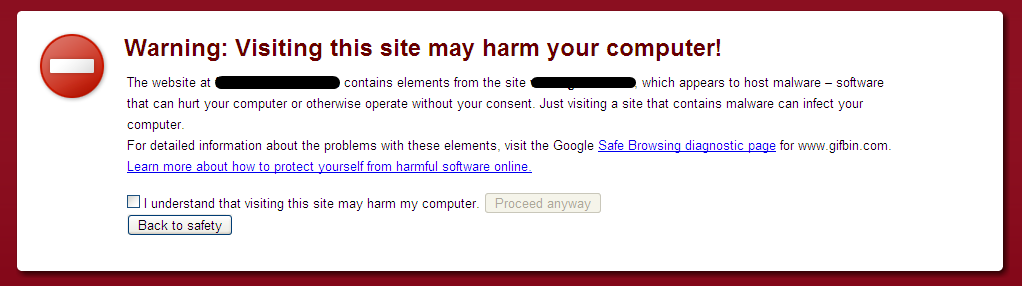
You can also check if Google identified malware or any other type of malicious code on your website from the Safe Browsing site status.
Check the web server and website control panel
Some hack attacks are very sophisticated. Some of them can also have an impact on the web server. For example, the attackers create users on the server’s operating system if they manage to escalate the privileges. Another common server level thing they do is a schedule to automatically re-infect the website if cleaned. Sometimes they store illegal torrent downloads or large files outside the web root. So it is a good idea to scan the whole operating system.
Run frequent security routine checks if you manage your own web server. Document all the operating system users, scheduled tasks (cron jobs) and files so when something changes you know of it. There are several commercial and non-commercial tools that can help you monitor your web server. If you have a managed solution use your provider’s control panel (such as CPanel) to monitor the scheduled tasks (cron jobs), ftp users and files.
Check all the log files
Last but not least, review all the logs. We have already mentioned the WordPress activity logs, however there are many other log files WordPress site admins should check. Log files contain a wealth of information if you know what to look for and where. From the log files you can find out exactly what has happened on your web server and WordPress site.
Keeping your WordPress Hacker Free
Identifying an attack early means less damage. It also means it is easier and it will cost less to fix. However, follow the below security best practices so your WordPress site does not get hacked in the first place:
- keeping a activity log and use it for your WordPress Intrusion Detection System (IDS),
- Use a security service or install a WordPress security plugin,
- Scanning your WordPress site for file changes to identify developers’ left-over files,
- Implementing strong password policies in WordPress.




The WordFence plugin has similar scanning functionality like Sucuri. I would also recommend looking into the Bullet Proof Security plugin.
Hi Jim,
There are several WordPress security plugins that do a very good job. I personally prefer and would recommend though to do most of the tasks done by a plugin manually (since they are one off tasks) and then use an online service to scan for malware. The reasons can be many, for example a malicious user can disable the plugin once the website is hacked, therefore you won’t get notified of the intrusion and infection.
I’ve tried a bunch of the security plugins and they’ve got a lot of useful features. However, I typically don’t like to have them active as they seem to take from system resources. A lightweight plugin or two to restrict brute force attacks is the way I go. And then the other plugins are activated now and again to do deeper scans.
Hi Mario,
Thanks for your feedback. Strictly speaking one does not need any “brute force” protection plugin. To protect your website from brute force attack all you need is a strong username and password. Of course you can add additional layers, such as HTTP authentication etc but that is just additional layers of security. You can read more about WordPress Brute Force protection from the article Protect your WordPress from Mass WordPress Brute Force Attacks
This was really informative. Your site is very helpful.
Thanks for sharing!
It is critical to be aware if your website has malware to minimize the damage. Many site owners including myself are not aware of the varied methods hackers use to manipulate a site for their own profit. Thanks for such an informative and educational article.
Correct Margie. In fact there have been cases where it took businesses years to realize that their website is hacked, which caused irreversible damage.
Thank you for such an informative article. I have found that if I keep my plugins and themes up-to-date as well as implementing strong passwords, I have avoided website malware. I intend to implement many of your helpful suggestions. i will definitely check out WP Security Bloggers.
Correct. In most cases keeping the software (plugins, themes and core) up to date and using strong passwords on WordPress does the trick.