Many administrators and site owners balk at the sight of failed login attempts on their WordPress site – yet, these are more common than you might think. While they’re not necessarily a threat to website security, understanding what they are and how to limit login attempts can help you ensure better website security.
In this article, we will go through what failed login attempts are, how to determine risk, and finally, how to set up a WordPress limit login attempts plugin.
What are failed login attempts?
Failed login attempts result from someone entering the wrong login credentials at the login page. This can be either the wrong username, password, or both. Failed login attempts fall into two categories – a user mistyping their credentials or a non-user trying to guess credentials. We will cover this in greater detail later in this article.
If you’ve recently come across failed login attempts on your WordPress site, don’t panic. By carrying out some quick troubleshooting, we can quickly find out whether these failed attempts are likely genuine or not.
Where to find a record of all login attempts
The easiest way to keep a record of all login attempts is by installing a WordPress activity log plugin like WP Activity Log. This WordPress plugin enables you to keep a record of all user and system activity on your website, including successful and failed logins and other suspicious activity.
Furthermore, you can easily set up WordPress events notifications that are sent to you via email or SMS whenever a particular activity occurs, such as a failed login.
WP Activity Log tracks two types of failed logins, giving you a clear picture of what is happening.
- Event ID 1002 tracks attempts to log in with a username that exists on your WordPress website but a wrong password
- Event ID 1003 tracks attempts to login in with a username that does not exist on your WordPress site
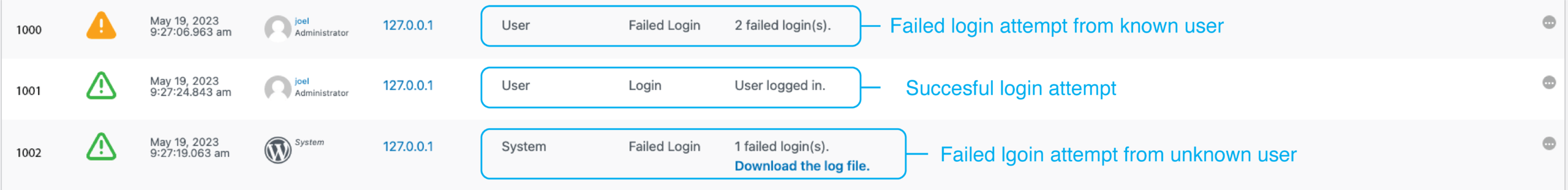
In the screenshot, you’ll notice the log keeps track of the following:
- The event ID as described above
- Severity of the event
- The date and time of the event
- The user that attempted to log in (this will show as System if the user doesn’t exist)
- Specific IP addresses from where the requests originated
- Object class, in this case, it’ll be either User (known user) or System (unknown user)
- Event type, telling us whether it was a failed login or a successful login
- The log message
You’ll also notice that System failed login events include a downloadable log file. This file will tell you which username was used for the failed login attempt.
You can view all logged activities through the Activity Log Viewer. If you’re running the premium edition, you can also filter for particular events, making it super easy to quickly find out whether there have been any failed login attempts, the time, their IP address, and other useful information.
As mentioned earlier, you can also set instant notifications and reports that are automatically sent out according to your preferred schedule.
Who’s trying to log in?
Failed login attempts can feel quite unsettling – however, not all failed login attempts should be cause for alarm. There are several reasons why you’re seeing multiple failed login attempts – these include:
Crawlers: The web is filled with creepy crawlies looking to harvest data. Legitimate crawlers, such as those used by Google and other reputable search engines, do not try to log in to websites. Not-so-legitimate crawlers, however, may attempt to log in.
Legitimate users: Anyone can forget their password, especially if they haven’t had their morning cup of coffee yet. This can be especially true if the person trying to log in does not use a password manager.
Many legitimate users fear forgetting their passwords and tend to use simple passwords that are easy to remember. The downside to this is that easy passwords are easy to crack – which may lead to a security breach. We will discuss this in a bit more detail later.
Hackers: Sometimes, failed logins result from hackers attempting to access your system. In most cases, hackers use automated bots to try many usernames and password combinations. This type of attack is called a brute force attack and comes in several flavors. Brute force attacks are essentially a trial-and-error approach to gain access by guessing usernames and passwords at random.
What are the risks of failed login attempts?
Not all failed login attempts are equally risky. We can quickly determine the level of risk by looking at the behavior of failed login attempts. We need to look at a few things:
Number of login attempts
A single or a few failed login attempts generally indicate a genuine user. On the other hand, a large number of persistent attempts may suggest that trouble is brewing. The number of failed login attempts should also take time into consideration – we will discuss this in more detail shortly.
Username
If all of the attempts are for one user account, check with the user whether they experienced any login issues. You should force a WordPress password reset for that account as a safety precaution. On the other hand, if you see many different WordPress users experiencing multiple failed login attempts, this might be a sign that someone is trying to breach your WordPress site.
IP address
The IP address can indicate quite a few things, including where the user is from. However, that user could be using a VPN, an onion router, or a proxy – thus masking their true IP.
You can also match the IP address to the username and see whether it’s the same IP they always use or it suddenly changed. Keep in mind that the user may have started to use VPN recently, so it’s worth investigating further before making any assumptions.
Time
Did the failed login attempts occur over a short period or a more extended period? In genuine cases, you can expect a low number of attempts, say between two and five, over an extended amount of time as the person trying to login in tries to remember their password as they question themselves over a cup of tea.
Hackers know they’ve probably got the wrong password, and they use a bot to help them attempt as many passwords as possible over a short period of time. Keep in mind that hackers can also choose to take the longer route and attempt a few different passwords every now and again to try to mimic human behavior.
How to limit failed login attempts on WordPress
The best way to set up limit login attempts is to use Melapress Login Security – our WordPress limit login attempts plugin that helps you implement different security measures for your login. The plugin offers tons of functionality; however, this article will focus on how to limit failed login attempts.
In this section, we will go through a tutorial on how to set up and configure the Melapress Login Security plugin.
Step 1: Download and install the plugin
Limiting login attempts is a premium feature of Melapress Login Security, included in the Business (from just $49/year) and Enterprise (from $59/year) editions. You can view all editions and buy a license here. We offer a 30-day money back guarantee, so you can try the plugin completely risk free.
Once you purchase the plugin you will receive an email with a license key and a download link. Download the plugin and install it through your WordPress dashboard just like any other plugin. Ensure you enter the license key when prompted to, and you’re all set to start configuring up our WordPress limit login attempts plugin.
Step 2: Enable policies
Melapress Security Login’s failed login policy forms part of the password and login policies. This security feature is designed to help you limit login attempts. To this end, you must first enable password & login security policies by navigating to the plugin settings Login Security> Login Security Policies. Check the Enable password & login security policies checkbox, then scroll down to Enable Failed Login Policies and check the checkbox.
Step 3: Configure your failed login policy

The Melapress Login Security policy configurator offers several configuration options, giving you the freedom to customize your policies to your needs and requirements.
- Number of login attempts before locking a user: This setting allows you to specify how many login attempts a user is permitted before their account is locked.
- Time period required to reset the failed logins count: Define how long the failed logins counter
- When a user is locked: Accounts on lockout can either be unlocked automatically after a lockout time has passed, or manually by an administrator.
- Required blocked users to reset passwords on unblock: You can choose to have genuine users whose account has been unblocked to set a new password.
Once you’ve made your selections, click on the Save Changes button to activate the policy.
Once you save the policy, it will be automatically activated for the WordPress login page. You can also activate the policy for 3rd party plugins such as WooCommerce, LearnDash, and others. Simply navigate to the Forms & Placement menu and choose from the available plugin integrations.
Additional steps for improved login security
As the old adage goes, prevention is better than cure. Having a failed logins policy is one of the best preventative measures you can take to limit login attempts in WordPress. However, there are other security measures you can take to ensure the continued safety of your WordPress website.
CAPTCHA
We also touched upon CAPTCHA – the ubiquitous test present in many logins and forms that is designed to let humans pass while stopping bots and other forms of automated attacks. The CAPTCHA 4WP plugin makes implementing such tests super easy while offering universal compatibility and support for different versions.
Two-factor authentication
In increasing the security of login processes, WordPress two-factor authentication is a must-have. Through this process, users need to authenticate a second time by entering a one-time passcode provided through their smartphone. By employing 2FA, which you can easily do through plugins such as WP 2FA, you can ensure that even if passwords get compromised, unless the person has the phone tied to that user account, they will not be able to log in.
Disable inactive users
Inactive WordPress user accounts are a prime target for bad actors since illegitimate activity tends to go unnoticed. With no upside to leaving them active, deactivating inactive accounts should be a no-brainer.
Inactive users can be disabled manually or automatically using Melapress Login Security. Once the account is disabled, users would need to get in touch to have their account reactivated. You can also choose to have the users reset their password on reactivation for additional security.
Going a step further (Optional)
With the password and failed login policies, CAPTCHA, and two-factor authentication in place, you should be well covered.
However, if you still experience large volumes of failed login attempts in WordPress, you should consider using a CDN service. You might want to speak to your web hosting provider to assist you with implementing a solution suitable for large-scale attacks.
WordPress password security requires a 360 approach
As we saw throughout the article, you must consider several factors when implementing a failed login policy. While limiting login attempts with a WordPress limit login attempts plugin is a good first step (and a necessary one), by taking a 360 approach, you can be that much safer. Not only does this help you cover all of your bases, but it can also help you inspire more trust and confidence in your WordPress website.
A 360-degree approach looks at several factors, including plugins and theme updates, two-factor authentication, etc. This way, you can ensure that your WordPress security is in tip-top shape to keep your site secure.
Frequently Asked Questions
Blocking IPs of failed login attempts in WordPress is often touted as one surefire way to cut off bad actors at the knees. While there is some truth to this, anyone can easily change their IP in seconds, potentially turning this exercise into an endless cat-and-mouse game.
If you have a limited number of users, you might want to consider whitelisting IPs instead, but keep in mind that most ISPs (Internet Service Providers) do not assign static IPs to their customers. Users might also choose to log in from a different location (whether it’s an emergency or otherwise), potentially turning whitelisting into a nightmare.
Unless you’re under a DoS (Denial of Service) or DDoS (Distributed Denial of Service) attack, failed login attempts in WordPress are not going to make a noticeable impact on performance. Of course, if you’re already using all available resources, you might see a negative impact on server load. This might also be the case if login attempts are at a high volume/high frequency.
Generally speaking, firewalls do not block failed login attempts. Keep in mind that a legitimate user can very easily forget their password. As such, blocking them at the firewall level might not be ideal in limiting login attempts. This is why Melapress Login Security is such an invaluable WordPress security tool, as it allows you to set rules and effectively limit login attempts.
There are several plugins available that limit login attempts. Since WordPress allows unlimited login attempts as part of its default settings, plugins offer a quick and easy solution to this security risk.
Melapress Login Security is a premium WordPress limit login attempts plugin that offers a well-rounded WordPress login security solution. It not only allows you to limit login attempts but also enables you to set password and inactive user policies to improve your site’s security.
’s security.



