We all know that plenty of WordPress sites are getting hacked each year. Is it because WordPress is an insecure system? Is it a global WordPress issue, or does it come from those webmasters’ actions? How, and why is it happening?
Whether you are running a personal blog, business website, or an eCommerce site on WordPress, the security of your website should be a priority. There can be many reasons due to which your site’s security is compromised. The most common reasons are weak passwords, users mistakes, outdated software and missing security updates.
In this article we use the latest statistics from the WPScan vulnerability database to highlight which are the most vulnerable WordPress components, and to make emphasis on the importance of running up to date software and installing the necessary security patches.
You can also find some interesting stats and facts about WordPress vulnerabilities, as well as a few recommendations. Let’s dive right in.
Table of contents
What is the WPScan vulnerability database?
Before we dive into the statistics, let’s explain from where we got these numbers. All data is retrieved from the WPScan vulnerability database, an online browsable version of WPScan’s data files.
WPScan is an open source automated WordPress black box security scanner. This scanner uses this data to detect known WordPress core, plugins and themes vulnerabilities in WordPress websites.
To date the WPScan vulnerability database contains 21,755 vulnerabilities, 4,154 of which are unique vulnerabilities.
WordPress, plugins and themes vulnerabilities overview
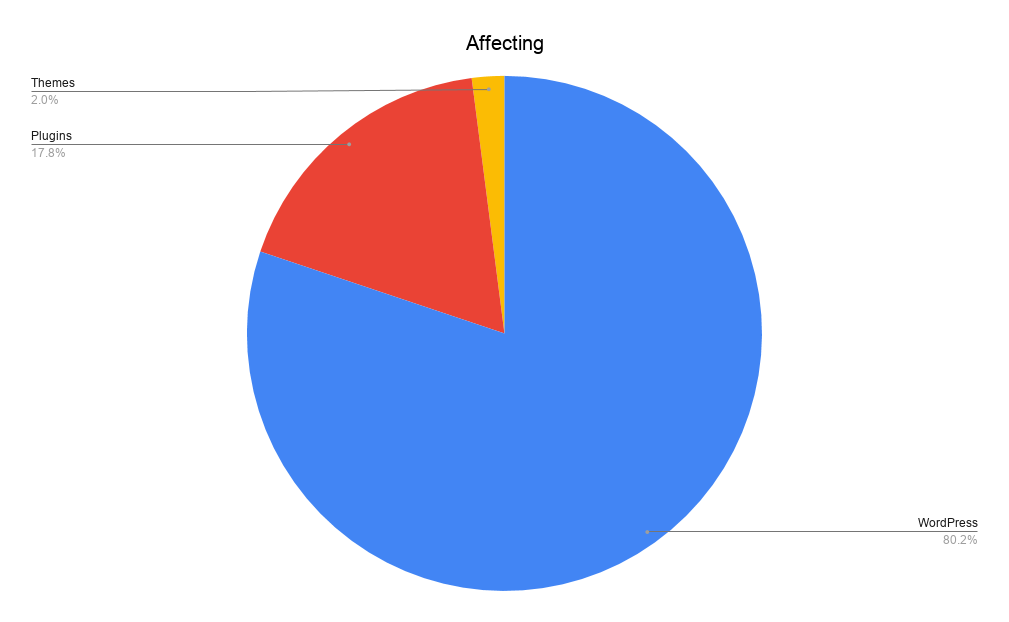
According to the WPScan Vulnerability Database, ~80% of the known vulnerabilities they logged are in the WordPress core software. But here’s the kicker – the versions with the most vulnerabilities are all way back in WordPress 3.X.
So far there are 17,467 WordPress core software vulnerabilities in the WPScan vulnerability database. Then there are 3,846 (17%) WordPress plugin vulnerabilities, and 442 (3%) WordPress themes vulnerabilities.
Why are there so many WordPress core vulnerabilities?
The number of vulnerabilities in the WordPress core are inflated in the vulnerability database because of the many versions of WordPress. Below is an explanation of why this happens;
A cross-site scripting vulnerability is found in a component in WordPress version 5.4.2. This component has been used in WordPress since version 3.7. Therefore all the previous released versions of WordPress are also vulnerable.
Therefore in the WPScan vulnerability database there will be one unique vulnerability, and 256 vulnerabilities!
So WordPress core as such is not insecure. It is very important to point out that WordPress core came a very long way and it’s much better and more secure software than it ever was.
Type of vulnerabilities in WordPress core, plugins & themes
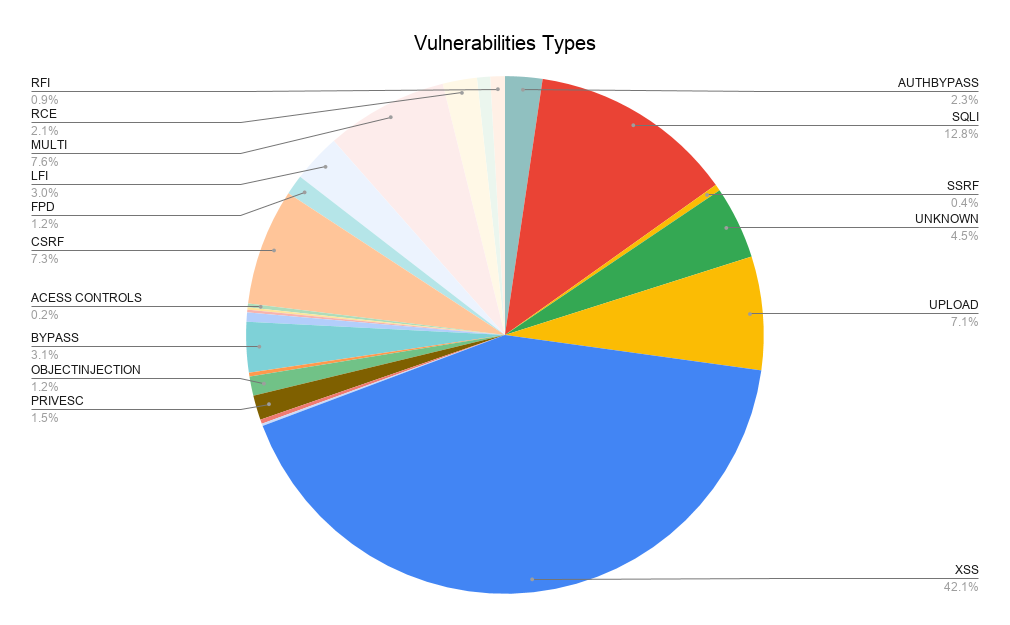
The most popular vulnerability types in WordPress core, plugins and themes are Cross-site Scripting and SQL Injection.
This is not surprising considering these 2 vulnerabilities have been listed in the OWASP Top 10 list of most common web security issues since its inception.
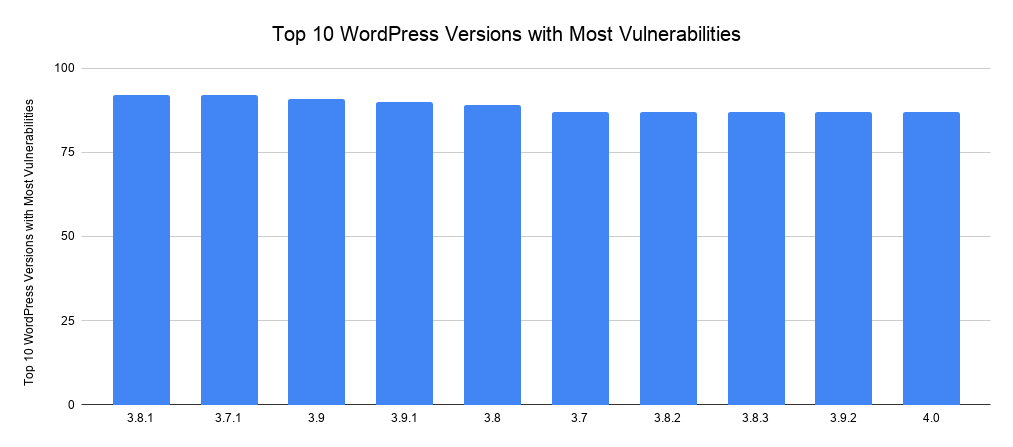
Statistics of WordPress core vulnerabilities
The below graph highlights the top 10 most vulnerable WordPress core versions, with versions 3.7.1 and 3.8.1 leading the pack with 92 vulnerabilities each. In second place, with 91 vulnerabilities is WordPress version 3.9.
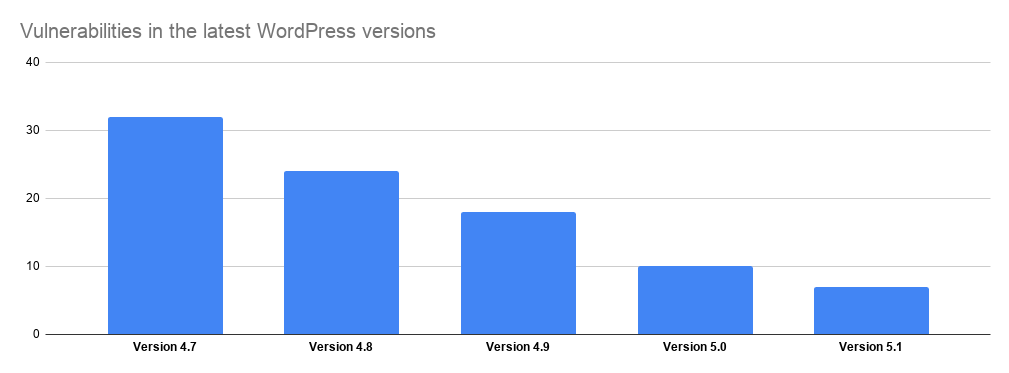
However, since then WordPress has definitely become more secure. Let’s take a look at the number of vulnerabilities in the last 5 versions of WordPress. As you can see the difference is quite big.
Top 10 most vulnerable WordPress plugins
Here are some facts about the Top 10 most vulnerable WordPress plugins:
NextGEN Gallery, NinjaForms and WooCommerce lead the pack with 22 vulnerabilities each.
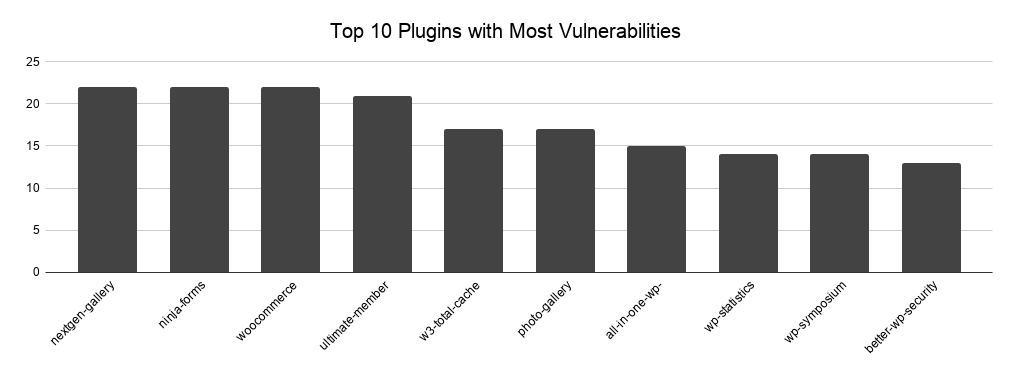
We were surprised to see All In One WP Security & Firewall, a WordPress security plugin in the Top 10 most vulnerable WordPress plugins. I am not saying such plugins are bulletproof. Though I would expect that a plugin that’s written by security people to have less vulnerabilities, or at least not to be in the top 10 list.
Top 10 most vulnerable WordPress themes
The below graph highlights the top 10 most vulnerable WordPress themes. The highest one has only 5 vulnerabilities under its name.
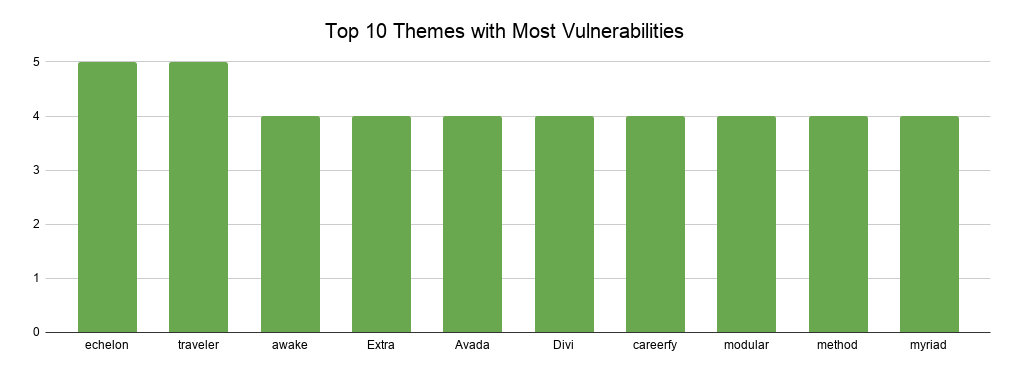
Themes tend to have much less vulnerabilities than plugins because they do much less in terms of functionality. For example, while most plugins handle data, user input and manipulate user data, themes mostly change the look & feel of WordPress websites.
What do these WordPress vulnerabilities tell us?
People love WordPress because of the huge array of available plugins and themes. As of writing this, there are over 57,000 plugins and more than 7,000 themes on the WordPress repository, and thousands of additional premium ones scattered across the web.
While all those options are great for making your site better, you should always do a little research before installing a plugin or theme to your WordPress website. While most WordPress developers do a good job of following code standards and patching reported security issues once they become known, there are still a few potential issues:
- The plugin or theme is no longer maintained,
- Developers take a long time to issue a security patch or are non-responsive,
- A plugin or theme has a vulnerability, however, since there is not much attention on it that vulnerability goes undetected.
Refer to how to choose the best WordPress plugin for your requirements for more details on this subject and how to determine if a plugin is a good choice for your WordPress website.
So what’s the takeaway?
In short, keep all your software up to date!
WordPress is one of the most popular CMS in the world, and if you follow security best practices and keep it up to date it’s very unlikely that your website experiences any issues.
Are these WordPress vulnerabilities statistics accurate?
These statistics are based on the information stored in the WPScan Vulnerability Database. Although it is frequently updated, it is by no means complete.
There are many other vulnerable WordPress plugins and themes that are not listed here. However, this gives us a good overview of the state of WordPress vulnerabilities.
Submit known WordPress vulnerabilities
The WPScan team encourages everyone who knows about WordPress core, plugin or theme vulnerabilities to submit the details to them.
Before submitting a new vulnerability, do a search in the database to ensure the issue was not submitted before. This will ensure we have one centralized and reliable source of information.
How to Ensure WordPress Security (security best practices)
Now that we have covered all potential and known vulnerabilities, let’s take a look at the different ways to secure your website.
The first thing is to regularly update your WordPress version. You should definitely develop the practice of updating your WordPress version and also, don’t forget to update your plugins and themes.
Here are some additional actions that you can do in order to secure your WordPress website:
- Avoid Using Common Passwords
When you have a strong password, any hacking attempt can be avoided or at least delayed.
- Set up a two-factor authentication login
Anyone who wants to log in to your WordPress website would have to go through one more step before gaining access to your account.
- Do not use nulled plugins and themes
It tempts almost everybody, however these free copies of premium plugins and themes more often than not are loaded with malicious malware. Support the developers of the plugins you use by buying the premium edition. It helps further develop the product, add new features and keep it secure.
- Use WordPress Security Plugins
Nowadays there is a huge variety of security plugins that are created to protect your website from various attacks. The best ones are updated regularly, which makes them capable of detecting any attempt of hacking and any addition to your code. We develop a number of WordPress security and site management plugins. Check them out!
To wrap up
Securing your website is super essential. Having a clear view of the threats and the tools that you can use to deal with the potential attacks is crucial. Your first and foremost priority should be to have and maintain a secure website.
As a result of its popularity, WordPress is a big target for hackers. That’s why you must go an extra mile to ensure your site’s safety. A secured site will surely embed trust in your potential customers, and hence, assist in the growth of your business.
Keep your website protected, and stay safe!




When you mention which plugins are the most vulnerable, you don’t mention what versions you’re referring to. This makes an enormous difference, especially when plugins like WordFence are updated frequently, (some could argue *too* frequently) and plugins like NextGen Gallery have been around for many, many years.
Do you have the version number information for these “most vulnerable” plugins?
Hi Kevin,
Very good point. What I am trying to highlight here is not if vulnerabilities have been fixed or not, but I am trying to raise awareness about writing more secure code to avoid such vulnerabilities in the first place.
When talking about WordFence and frequent updates I see your point, and yes reported issues have been fixed and that is good. But the security history of a plugin (or any other software) tells us a lot about the product, for example in this case security was not catered for in the first place when developing the plugin and this is a bit of a let-down considering the plugin is written by security people who are aware on what type of vulnerabilities attackers / hackers typically exploit. In fact I am not just surprised about Wordfence but about all the 5 commercial plugins listed there!
Can commercial plugins have vulnerabilities? Of course they can, everyone can do mistakes but they should lead by example and not be in the top 10 list of plugins which had most reported vulnerabilities so far. It is not exactly something one should boast about ay?
Had the vulnerabilities not been dealt with, then I would probably agree with you. When a plugin is under active development and performs many useful functions – like WordFence – I’m not too concerned about it being less secure than the (hopefully rock-solid) Hello Dolly plugin.
Just my 2 cents worth…
Hi Kevin,
I agree and disagree with you. I mean I appreciate the fact that for example the WordFence developers do address security issues in a timely manner but I do not appreciate the fact that their history has so many vulnerabilities. It clearly shows that they do not practise what they preach; i.e. security should be thought of in everything you are doing, especially when developing a plugin. But hey, aren’t we all entitled for an opinion? 🙂
I am shocked – SHOCKED – Wordfence has any vulnerabilities.
Tim
I wouldn’t be so surprised. Every software can have vulnerabilities. As explained in the article, what’s important is how the developers respond to such vulnerabilities.
Hey Robert,
thanks for sharing these statistics with us!
I’ll have to share them with some of my friends who run online businesses. I’m preaching about updating their sites for ages and now they finally have the evidence that running WordPress 3.6 isn’t a good idea when you have 100k uniques and more every month 😉
Hopefully you’re not only raising awareness for writing secure code, but also for maintaining WordPress more carefully.
Cheers,
Jan
Yes but if you use your thought about overall history, then why would anyone use WP at all judging by its history as they update bad security all the time
Hi Chris,
Thank you for your comment.
What we are trying to highlight here are a few things;
1. First of all the importance of security code audits. If you are writing a plugin especially for commercial purposes it is recommended that you do frequent security code audits to ensure that you ship the best and most secure code when possible.
2. I am not saying that plugins with many vulnerabilities are not good. What I am trying to say is that one would expect better from a security plugin. Having said that as long as the developer addresses the issue in a timely fashion it is all good, though there might be the day when someone discovers a vulnerability and not report it. This would allow him to exploit the vulnerability (0-day exploit). Therefore if you choose a plugin which has a “good history” the chances of being a victim of a 0-day exploit are much lower.
As regards your comment with WordPress, you are right. In fact WordPress’ history is not that bright in terms of security but developers are indeed taking a new more proactive approach when coding. Having said that yes, WordPress still got a long way to go when it comes to security.
Good information and I’ll use wpvulndb.com to see what I’m dealing with. But I accept the fact that vulnerabilities exsist (but don’t like it :-)), if we see to WP in general, even the use of WP can be seen as unsafe.
What’s far more interesting for me is if and how quick the developper reacts and solves the vulnerability-problem. And how the communication is with their userbase. Is the program automatically updated or is this the webmaster the one who must initiate the update?
If the update is very quick and the communication good… I’ll appreciate that and see that as a plus for that developer and gives me trust.
Hello Bernard,
Have a look at http://www.wpsecuritybloggers.com and subscribe to it. It is a central source of WordPress security news, i.e. an aggregation of most popular WordPress security sites.
This post last updated in Apr 2019! More than a year ago. I recommend updating the stats about vulnerable plugins and themes a little bit. Also, the post should include that one of the main reasons a WordPress website gets hacked or affected by malware beacuse of null plugins and themes. I have fixed lots of sites and in those, most of them are affected due to themes and plugins from unverified sources.
Thank you for your feedback Jafor. Indeed, we are currently in the process of updating this article.
When I read your article, I understood that 80% of vulnerabilities were in WP core but the statistics from WPScan itself paint a totally different picture that 88% of vulnerabilities come from plugins. https://wpscan.com/statistics
Can you comment?
Hi Christine,
Thanks for reaching out!
The number of vulnerabilities in the WordPress core are inflated in the vulnerability database because of the many versions of WordPress, as explained in the article. Below is an explanation;
For example, a cross-site scripting vulnerability is found in a component in WordPress version 5.4.2. This component has been used in WordPress since version 3.7. Therefore, all the previous released versions of WordPress are also vulnerable.
Which means that in the WPScan vulnerability database there will be one unique vulnerability, and 256 vulnerabilities!
I hope this clears things up.