It is very easy to identify the usernames on an out of the box WordPress installation. Though, there are several WordPress hardening techniques you can implement to hide the usernames, such as the ones mentioned below. However, these only make it a bit more difficult to guess the usernames, but they do not solve the problem.
In fact, it is still possible to guess the usernames, even after applying them. Below is one example of how easy it is to guess usernames on a WordPress system.
WordPress username disclosure
When you try to login to a WordPress site using a username that does not exist on the system, the response indicates that an invalid username was used. The error message itself is invalid username.
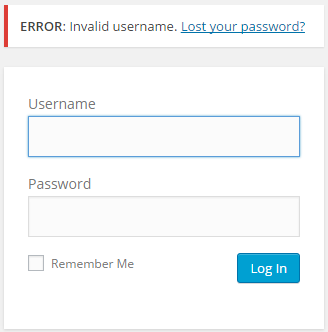
If you try to login using a valid username and a wrong password, WordPress’ error message indicates that the password for the username is incorrect. WordPress also retains the username in the response, thus disclosing it. The error message also confirms this; The password you entered for the username admin is incorrect.

Is the WordPress username disclosure a real problem?
Many other vendors, including big ones such as Microsoft and Cisco, have had this same identical problem in the past. Most vendors addressed this issue because many security professionals consider this to be a security flaw. In fact, in 2009 it was reported as a security issue in WordPress. The CVE number is CVE-2009-2335.
It was also reported on the WordPress Trac in a ticket. In the Trac ticket, one of the WordPress core developers explains that there are many other ways how to reverse engineer a WordPress username, so they will not address this issue. In fact you can easily enumerate the WordPress usernames with WPScan.
So, is this really a security issue? It could be considered as an issue, especially since it was considered to be an issue with other vendors. However, let’s look at the bright side.
The solution to the WordPress username disclosure
There are many things you can do on WordPress to mitigate this issue. As such, by following these best practises, username disclosure will be the last worry on your mind.
- Use policies to enforce strong WordPress passwords,
- Enable 2FA with a WordPress two-factor authentication plugin.
These alone, should be more than enough. However, if you want to go paranoid mode, you can also implement the below, especially if you do not have any guests logging in to your website and all users have a fixed IP address.
- Add HTTP authentication for the WordPress login page,
- Restrict access to the login page (/wp-admin/) section via IP addresses.
That should be it. And to always be on the safe side, and to make sure you know what is happening on your WordPress site, install an activity log plugin to keep a record of all the changes that happen on your website.



